Home | Projects | Notes > ARM Cortex-M3/M4 Processor > Stack Analysis Using __attribute__((naked)) Function
Stack Frame Analysis Using __attribute__((naked)) Function
Introduction
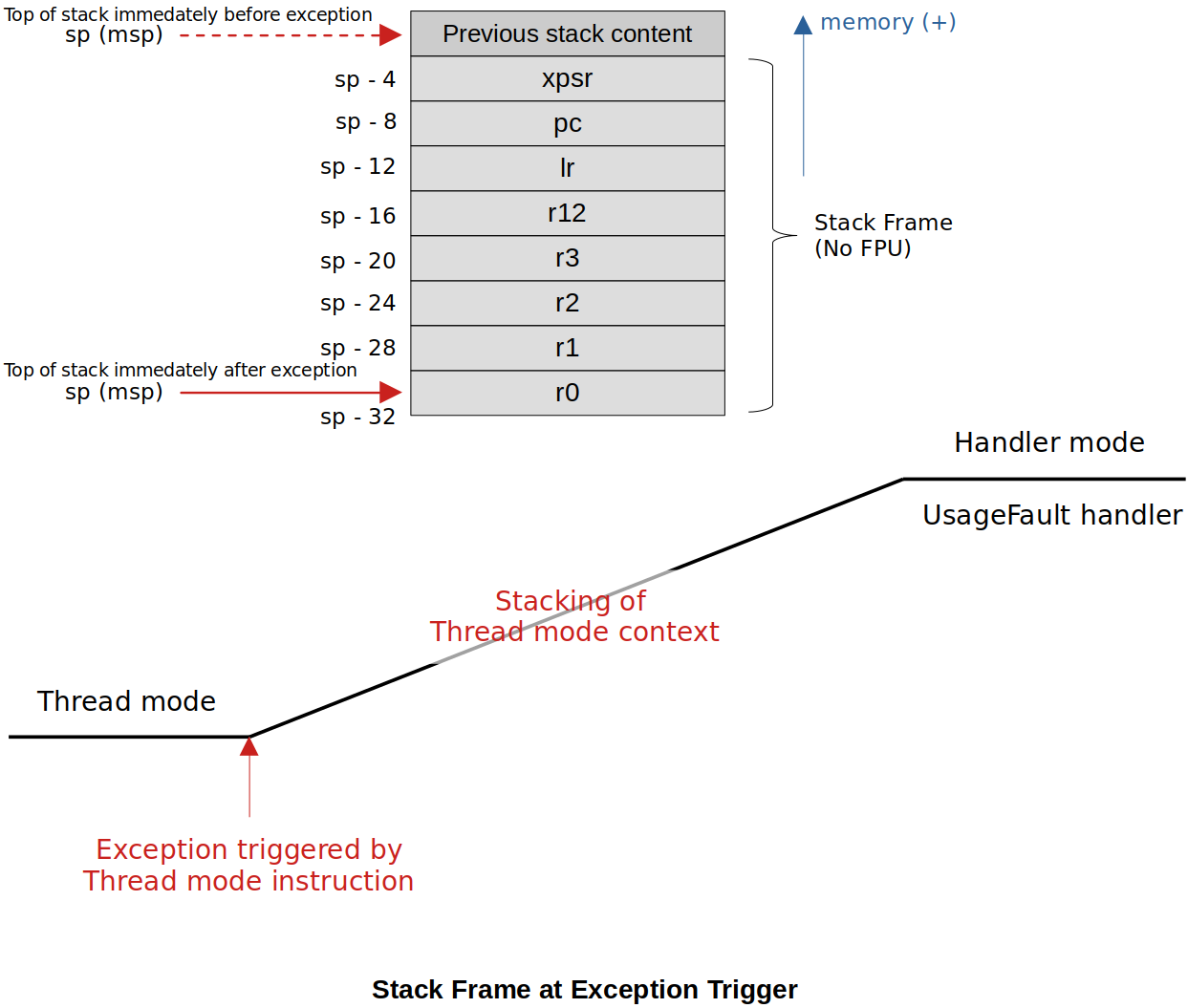
At times, you may want to analyze the stack frame pushed onto stack immediately after the exception has triggered to understand what exactly has gone wrong in the Thread mode code.
In this case, if you understand the processor's stacking process at exception trigger you will be able to print the contents of the pushed stack frame and analyze them. The key here is to obtain the stack pointer immediately after the exception has triggered.
Prologue & Epilogue of a C Function
Every C function will be added two sections called "Prologue" and "Epilogue" when the compiler generates the assembly code for it.
Prologue - What happens at the beginning of a function. Its responsibility is to set up the stack frame of the called function.
Epilogue - What happens last in a function. Its purpose is to restore the stack frame of the calling function. (The exact opposite of Prologue).
When debugging the following code, you'll realize that the compiler automatically generates some assembly code that manipulates SP before the first line of
UsageFault_Handler().xxxxxxxxxx131// Stack frame analysis using UsageFault_Handler()2// First mission is to secure the stack pointer (MSP) immediately after the exception trigger.34void UsageFault_Handler(uint32_t *pBaseStackFrame)5{6__asm("mrs r0, msp"); // secure MSP and store it in r07register uint32_t msp_value __asm("r0"); // copy MSP into C variable msp_value8uint32_t *pMSP = (uint32_t *)msp_value;9uint32_t *pUFSR = (uint32_t *)0xE000ED2A;10printf("Exception: UsageFault\n");11printf("UFSR = %lx\n", (*pUFSR) & 0xFFFF);12while (1);13}L4: Notice the keyword
registerhas been used so thatmsp_valuedoesn't consume stack memory, and use a register to keep its value instead. This prevents the stack pointer from being updated.To secure the stack pointer (MSP) immediately after the exception trigger without allowing the prologue to manipulate it, you need to use
__attribute__((naked))functions.
Stack Frame Analysis Using __attribute__((naked)) Function
This attribute tells the compiler that the function is an embedded assembly function. You can write the body of the function entirely in assembly code using
__amsstatements.The compiler does not generate prologue and epilogue sequences for functions with
__attribute__((naked)).Use naked functions only to write a group of assembly instructions (
__asmstatements). Introducing regular C code might not work properly.Now using a
__attribute__((naked))function, we can re-write the previous incomplete stack frame analysis code as follows:xxxxxxxxxx461/*2* The function prologue is a few lines of code at the beginning of a function,3* which prepare the stack and registers for use within the function.4* Similarly, the function epilogue appears at the end of the function and restores the stack5* and registers to the state they were in before the function was called.6*7* So, if you want to secure the stack pointer right after the automatic stacking is carried out,8* it is important that you store the SP before the function prologue further manipulates the stack.9* One way to work around this situation is to use __attribute__((naked)) function.10*/1112__attribute__((naked)) void UsageFault_Handler(void)13{14/*15* Here we capture the value of MSP which happens to be the base address of the stack frame16* which got pushed onto stack automatically by the processor during the exception entry17* from Thread Mode to Handler Mode.18*/1920__asm("mrs r0, msp"); /* Secure MSP and store it in r0. (According to AAPCS,21the value stored in r0 will be passed to the callee22as the first argument. Therefore, secured MSP value23will be passed to the first parameter of the24UsageFault_Handler_C '*pBaseStackFrame'. */25__asm("b UsageFault_Handler_C"); /* Branch to UsageFault_Handler_C */26}2728/* UsageFault handler */29void UsageFault_Handler_C(uint32_t *pBaseStackFrame)30{31printf("Exception: UsageFault\n");32printf("UFSR = %lx\n", UFSR & 0xFFFF); /* Read 16 bits only */33printf("MSP = %p\n", pBaseStackFrame); /* print */3435/* Print stack frame (to troubleshoot any potential issues occurred when in Thread Mode) */36printf("r0 = %lx\n", pBaseStackFrame[0]);37printf("r1 = %lx\n", pBaseStackFrame[1]);38printf("r2 = %lx\n", pBaseStackFrame[2]);39printf("r3 = %lx\n", pBaseStackFrame[3]);40printf("r12 = %lx\n", pBaseStackFrame[4]);41printf("lr = %lx\n", pBaseStackFrame[5]);42printf("pc = %lx\n", pBaseStackFrame[6]);43printf("xpsr = %lx\n", pBaseStackFrame[7]);4445while (1);46}L7: According to the AACPS, the contents of r0 will be passed to the callee as the 1st argument. This way we can capture the SP we want and pass it to the 1st argument
pBaseStackFrameofUsageFault_Handler_c().L17: Now
pBaseStackFramecontains the SP value immediately after the exception trigger which is not yet been manipulated by the prologue of this function.CubeIDE also provides functionality of capturing stack frame for the analysis purpose. Check out the"Fault Analyzer" window during the debug mode.
References
Nayak, K. (2022). Embedded Systems Programming on ARM Cortex-M3/M4 Processor [Video file]. Retrieved from https://www.udemy.com/course/embedded-system-programming-on-arm-cortex-m3m4/